Generally, information security is the process of protecting information from unauthorized access. This is done through different processes, such as authentication, encryption, data destruction, and network security. In addition, information security may also include business continuity and disaster recovery.
It’s important to understand that information security is more than simply preventing unauthorized access. It’s also about preventing damage and destruction of data. If a hacker is able to access information, they can manipulate or alter it in a way that will make it unusable. Information security requires a flexible mindset and an appetite for continuous learning. Information security professionals need to have a comprehensive understanding of computer technologies, as well as the skills needed to respond to security breaches quickly.
Information security is a field of study that spans a variety of academic disciplines. However, the main focus of information security is the protection of computer-based data. This includes both digital data and physical information. The field is vast, and there are many different types of jobs available. Information security specialists can specialize in auditing, security testing, and event management.
The most important element of information security is confidentiality. This means that information cannot be accessed by unauthorized parties, such as hackers or competitors. This can be achieved by limiting access to specific individuals or through technological means. For example, an accounting analyst may be able to alter financial data, but technical controls can prevent him from doing so. In some cases, the best way to limit a person’s access is to hire a security guard.
Other aspects of information security are availability and integrity. Availability is the principle that information is available when needed. The availability of information is influenced by various factors, such as software and hardware. If there are any changes to the system, such as a new security patch or malware, it is important to know that they are being properly managed. Some examples of breaches of availability include the Colonial Pipeline attack, which took down a large portion of the federal government’s network, and Solarwinds, which crashed an important government website.
The CIA has developed a triad of information security: confidentiality, availability, and integrity. The triad is a set of principles that organizations should use to measure their risk. When an organization implements a new system, they can apply these principles to assess how much risk they are taking. These principles can help them to put in place guards and mitigations to reduce risk.
In addition to protecting the security of information, the triad also explains how information is managed, from authentication to encryption. These systems are designed to help enterprises protect their data in the event of a breach. Information security managers implement these systems, which include tools to monitor the integrity of data. The integrity of data is important when it comes to legal rights. It’s also a good idea to make changes to data in a way that accidental changes can be recovered.
Information security vs cybersecurity
Since information Security has become the recognized corporate buzzphrase that essentially means “computers and related stuff,” you can also see the interchangeable use of information security and cybersecurity. Cybersecurity is, generally speaking, the broader practice of protecting IT assets from attack, and under the cybersecurity term, information security is a particular discipline. InfoSec’s sister activities are network security and application security, focusing on networks and app code, respectively.
There’s some overlap here; if Data transmitted over an unreliable network or exploited by a leaky application may not be protected. There is also plenty of information that needs to be secured and that is not stored electronically. Thus, the remit of InfoSec pro is inherently broad.
Information security principles
The so-called CIA triad most frequently sums up the basic components of information security:
- Confidentiality is probably the triad aspect that comes to mind almost instantly when you think of information security. Data is confidential if this can only be done by those allowed to access it; you need to distinguish who is attempting to access data and block attempts by those without permission to maintain confidentiality. All the methods designed to ensure confidentiality are passwords, encryption, authentication, and protection against intrusion attacks.
- Integrity: After all, a hacker can not modify information they can not access, but other resources help provide comprehensive protection of integrity: checksums can help you verify data integrity, for example, and version control software and regular backups will help you restore data to a correct state if appropriate. Many of the methods that guarantee confidentiality will also ensure data integrity. Integrity also covers the principle of non-repudiation: you must be able to show that, particularly in legal contexts, you have upheld the integrity of your records.
- Availability is the confidentiality mirror image: while you need to ensure that unauthorized users can not access your data, you also need to make sure that those with the correct permissions can access it. Ensuring data availability requires balancing the amount of data access you expect from network and computing resources and enforcing a good backup strategy for disaster recovery purposes.
Your data must always be kept private, in its correct state, and usable in the ideal world; in fact, you also have to choose which standards of information to prioritize. That enables the data to be analyzed. For example, if you store sensitive medical information, you would concentrate on confidentiality. At the same time, a financial institution can prioritize data integrity to ensure that nobody’s bank account is wrongly credited or debited.
Information Security Policy
A security policy takes the form of how these concepts are applied to an entity. This is not a piece of hardware or software for security; instead, it is a manual that an organization draws up to decide what data needs to be secured and in what ways, based on its own unique needs and quirks. These policies direct the company’s decisions concerning acquiring cybersecurity resources and mandate employees’ conduct and obligations.
Among other items, Your business information security policy should include:
- A statement outlining the purpose of the InfoSec program and your overall goals
- Definitions of keywords used to ensure mutual interpretation in the document
- An access control policy specifies who has access to what data and how their rights can be defined.
- Password guidelines
- To ensure the information is still accessible to those who need it, a data support and operations plan.
- Roles and duties of workers when it comes to data safety, and who is responsible for information security
One important thing to bear in mind is that your security strategy needs to protect more than just the assets you own in an environment where many businesses outsource certain information services or store data in the cloud. From personally identifiable data stored on AWS instances to third-party vendors who need to authenticate to access confidential corporate information, you need to know how you can deal with anything.
Measures for Information Security
As should be evident by now, just about all the cybersecurity-related technological measures apply to information security to a certain degree. Still, it is worthwhile to think about InfoSec measures in a big way:
- The hardware and software securing data, everything from encryption to firewalls, are technological steps.
- Organizational steps include establishing an administrative unit dedicated to information and incorporating information into each department’s roles.
- Human acts include providing consumers with awareness training on correct InfoSec practices.
- Physical controls require regulation of access to office locations and data centres, in particular.
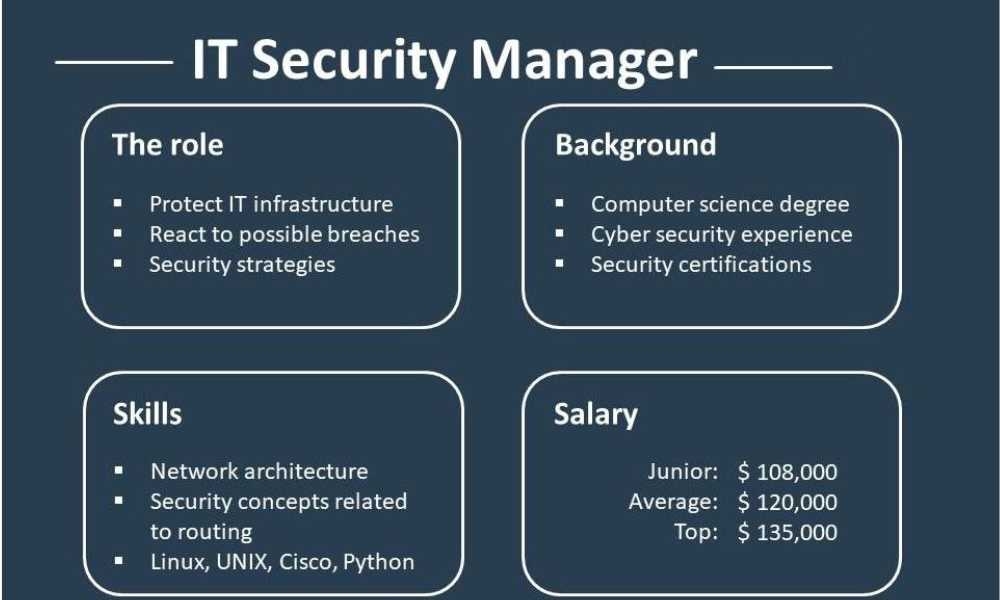
Jobs and Salaries
It’s no secret that cybersecurity jobs are in high demand, and according to Mondo’s IT Security Guide, data security was at the top of every CIO’s recruitment wishlist in 2019. There are two key reasons; many high-profile security breaches have resulted in harm to corporate finance and credibility. Most businesses continue to store customer information and offer access to it to more and more departments, raising their potential attack surface and making it more and more likely that they will be the next target.
In the field of Infosec, there are several different work names. In different industries, the same job title can mean different things, and you should also bear in mind our caveat from the top: many people use “information” to mean “computer stuff,” so some of these positions are not confined in the strict sense to just information security. But one can draw general conclusions.
Information security analyst: Jobs and Salary
Let’s look at one such job: information security analytics is generally towards the entry-level ever path for InfoSec. Christina Wood from CSO explains the work as follows:
Usually, security analysts deal with data protection (data loss protection [DLP] and data classification) and threat protection, including information security and event management (SIEM), user and organization behaviour analytics [UEBA], intrusion detection system/intrusion protection mechanism (IDS/IPS), and penetration testing. Key tasks include
- The management of security measures and controls,
- The monitoring of security access,
- The execution of internal and external security audits,
- The review of security violations,
- The recommendation of tools and procedures,
- The implementation of software,
- The teaching of security awareness, and
- The coordination of security with external suppliers.
Information security analysts are certainly one of those positions where there are not enough applicants to satisfy their demands. More than 100,000 vacancies in the United States for information security analysts in 2017 and 2018 were unfilled. This suggests that the infosec analyst is a lucrative gig: the median salary was pegged at $95,510 by the Bureau of Labor Statistics (PayScale.com has it a little lower, at $71,398).
Courses and training
How does one get information security? A computer science undergraduate degree does not hurt, but it is by no means the only way in; technology remains an industry where involvement in open source projects or hacking collectives, for example, can act as a valuable calling card.
Infosec, however, is becoming increasingly professionalized, meaning that organizations are providing more through formal certificates. Graduate degrees focused on information security are now offered by several universities. These programs could be better suited for those already in the field looking to develop their experience and show that they have what it takes to climb the ladder.
InfoSec’s free and low-cost online courses are at the other end of the spectrum, all of them relatively narrowly oriented. Tripwire breaks down eleven widely respected providers providing information security courses that could be worth your time and effort; the world of online training is something of a wild west.
Certifications
You may want to look at an information security qualification if you are already in the field and want to keep up-to-date on the latest trends, both for your own sake and as a signal to future employers. Among the top certifications for analysts in information security are:
- Systems Security Certified Practitioner (SSCP)
- Certified Cyber Professional (CCP)
- Certified Information System Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- GCHQ Certified Training (GCT)
Many of the Tripwire-listed online courses are designed to prepare you for these certification tests.