API Sеcurity Stratеgy is the lifeblood of the today’s digital ecosystems, allowing different apps, services and devices to work together in a cohesive manner. Despite their popularity, they have also become a high profile target for cyber attacks. Building a strong API security barrier is a must to protect sensitive information, comply with the regulatory requirements and to keep the digital services safe and sound. This post explores common mistakes and pitfall businesses make when designing their API Sеcurity Stratеgy and guidance on how to defend against them.
Understanding API Sеcurity Stratеgy
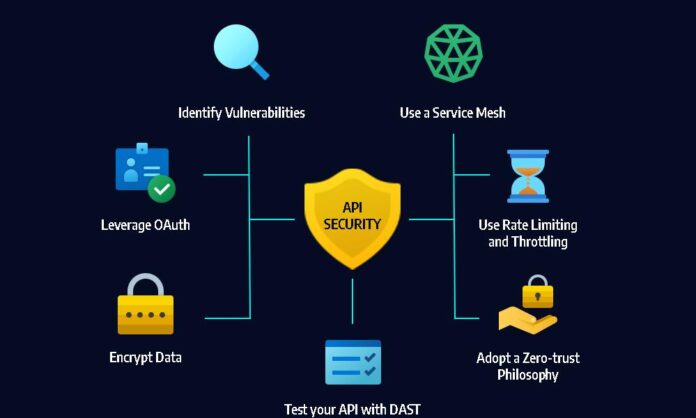
An API Sеcurity Stratеgy refers to the policies, systems, and tools which are executed to safeguard APIs from unauthorized or malicious access and abuse. It means protecting every stage of the API lifecycle—from conception and coding to deployment and monitoring. It is a complete solution comprising the following:
- Authentication and Authorisation: Confirming who is and is not allowed to access the API.
- Data Encryption: Data encryption ensures data is protected both on the move and at rest from unauthorized access.
- Input-Validation: Making sure that input by our users is safe and in the expected formats.
- Rate Limiting: Traffic management by capping the amount of requests to avoid misuse and ensure service accessibility.
- Observability: Always watch the API usage and look for anything that is suspicious and can quickly respond to it.
Common Mistakes in API Sеcurity Stratеgy
1. Neglecting Authentication and Authorization
One of the most common API security vulnerabilities is the lack of strong authentication and authorization controls. Strong authentication and good authorization policies must be implemented to help avoid this sort of unauthorized access. Not doing so can result in data leaks and actions that you wouldn’t necessarily like to be done in your system.
2. Insufficient Input Validation
Injecting untrusted input can result in injection attacks, including SQL injection and cross-site scripting (XSS). All input must be validated and cleaned to conform to expected formats and avoid malware. This is useful to avoid attacks which compromise vulnerabilities in crafted inputs.
3. Ignoring Rate Limiting
Without a per-application throttling mechanism, APIs are extremely vulnerable to DoS attacks, where attackers flood the system with requests. By enforcing rate limiting, the API can manage traffic better, maintain service availability, and avoid abuse.
4. Lack of Encryption
Sending sensitive information through non-secured channel has the risk of eavesdropping and manipulation. HTTPS with strong cipher suites helps keep your data safe and secure during transmission by preventing man-in-the-middle attacks.
5. Absence of Comprehensive Monitoring and Logging
Without good monitoring and logging, seeing a security incident is hard. They built strong logging and real-time monitoring solutions which provides the opportunity to get ahead in case of anomalies and for a quick response to an incident.
Best Practices for Crafting a Robust API Security Strategy
Receiving and remitting information from an API is crucial to the modern online experience, and businesses in most industries rely on these services to make important decisions. Here are some best practices for creating a strong API security strategy
1. Implement Defense-in-Depth
Using a defense-in-depth strategy guarantees that if one bad security measure does fail, there are other security measures in place to protect APIs. This approach uses a collection of security techniques which include firewalls, intrusion detection systems and access controls.
2. Regularly Update and Patch Systems
The software and systems must be kept up-to-date, as that is one important measure in defense against known vulnerabilities. Frequently updating with the latest security patches serves to close off any potential security holes and improves the API infrastructure’s security layer, ensuring a solid API security strategy.
3. Conduct Security Audits and Penetration Testing
Security audits and penetration testing on a frequent basis can discover and patch vulnerabilities before they’re exploited. Proactive security assessments help to future-proof an API security strategy, capable of dealing with a constantly evolving threat landscape.
Importance of API Security Strategy Across Sectors
1. Financial Services
In finance, they’re used to provide instantaneous transactions as well as access to sensitive financial data. An Effective API Security strategy Solution is a Must to Counter Fraud, Unauthorized Access, and Data Breaches The need for robust API security integration and measures cannot be overstated. The integrity and confidentiality of financial transactions is preserved by employing strong authentication, encryption and monitoring.
2. Healthcare
APIs are used by healthcare entities to share patient data and connect disparate health systems. An effective API security strategy is important to secure these APIs, not just to comply with regulations such as HIPAA, but also to safeguard patient privacy. Enforcing access controls, encryption, and conducting periodic security assessments helps protect personal health information.
3. E-commerce
E-commerce websites use APIs for payments, inventory and customer chats. An insecure API may cause monetary loss and customer trust loss also. By using safe coding practice, input validation, and transaction monitoring, it prevents fraud and a safe shopping experience.
4. Government
APIs are used by government agencies to deliver services to the public, and access to citizen information. Safety these APIs is critical to the prevention of unauthorized access and to encourage public trust. Tight access controls, encryption and adherence to regulatory standards protect government systems.
Advantages and Disadvantages of API Security Strategy
Advantages
- Greater Data Security: A more holistic approach to API security helps ensure that sensitive data is safeguarded against unauthorized access, misuse or breaches.
- Regulatory Compliance: Companies adopt security to comply with regulations because it prevents them from facing legal consequences.
- Greater Trust: Investing in API security helps to instill confidence with customers and partners and create closer ties to drive business forward.
- Less Chance Of Cyberattacks: taking steps to protect your network can help you eliminate security holes in your network, and by being proactive you are less likely to experience an attack.
Disadvantages
- Complexity: The work involved in building and overseeing a strong API security strategy may be complex, budget- and resource-wise.
- Potential Performance Overhead: Introducing security (e.g., cryptography and throttling) could lead to potential performance overhead.
- Ongoing Monitoring: API security needs to monitor how things are developing and update to support evolving threat-profiles and type of vulnerability.
Conclusion
API security strategy illustration depicting key practices like encryption, authentication, and monitoring to protect data and prevent breaches. It will still be essential to look over your shoulder when it comes to putting together a strong API security strategy. Organizations can protect their APIs against those types of increasingly sophisticated attacks by not making some classic mistakes and following best practices. Periodic review and adjustment of security processes is critical in order to ensure that security remains strong in such as open and interconnected digital world.