PHP is still going strong being the heart of web development, everything from trivial blogs to huge enterprise systems. At the core of most PHP applications is a database, the connection between your code and your data. Today, we are going to build a thorough but clean and simple PHP database class that will make all your database tasks easy and not awkward at all, and speed up your development so you can have a life!
Why Your Projects Deserve a Custom PHP Database Class
Think about constructing a house without any power tools. You could do it, but everything would take longer, and the results wouldn’t be as accurate. That’s what you get when you have raw database queries everywhere in your code base. A proper database class is your PHP applications very own tool bag.
On The Importance Of Clean Architecture In Modern Web. Code on Modern web apps require security, speed and clean architecture. An exclusive database class makes all three available. It serves as a barrier between your code and an attacker, protects against inefficient queries, and leaves your code beautifully clean and simple. The best part? Once you construct it, you can put this powerful weapon in your application utility belt and use it for all your projects.
Laying the Foundation: PHP Database Connection Mastery
All great work must have a base and our database class is no exception. It’s first the connection handling where any success starts. For MySQLi and PDO, we are spoiled in 2025. PDO would give us database agnosticism, but MySQLi will offer better performance when we know we’re targeting a MySQL/MariaDB system – and it’s what we’ll use for our sample script.
<?php
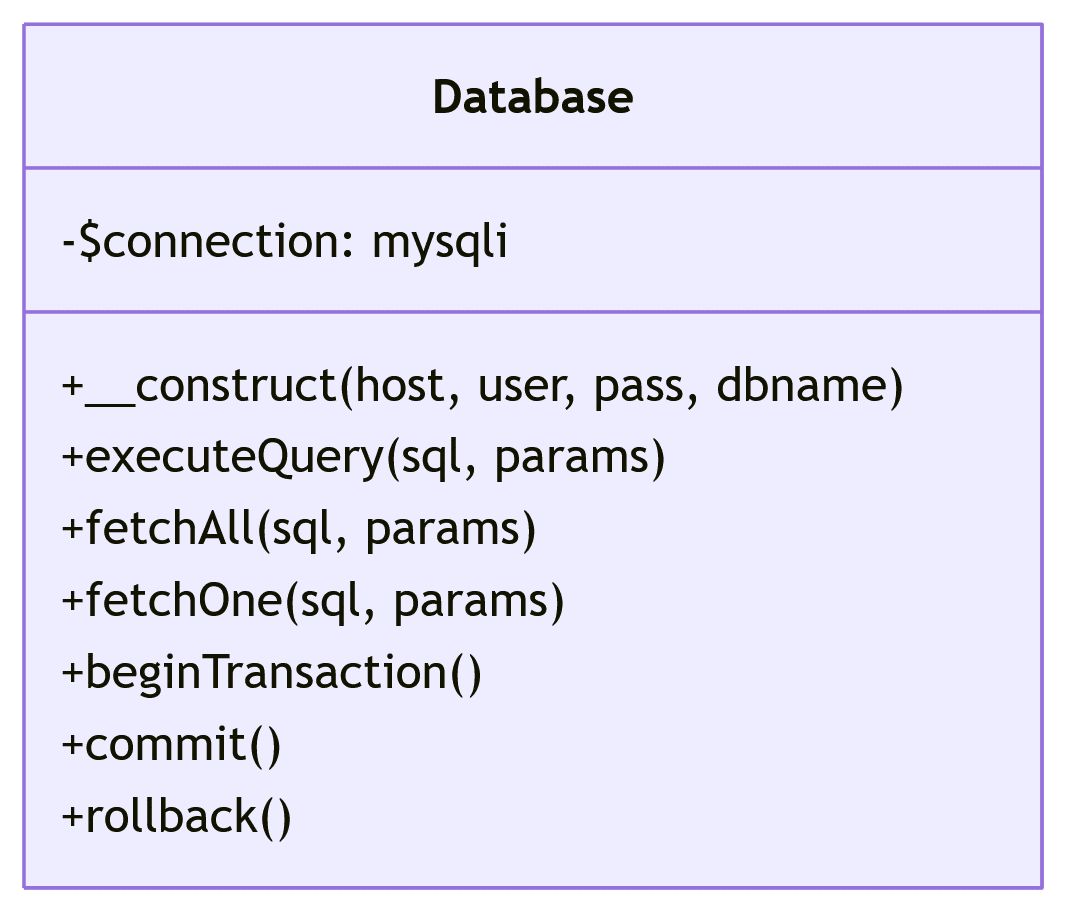
class Database {
private $connection;
public function __construct($host, $username, $password, $database) {
$this->connection = new mysqli($host, $username, $password, $database);
if ($this->connection->connect_error) {
throw new RuntimeException(
"Database connection failed: " . $this->connection->connect_error
);
}
$this->connection->set_charset("utf8mb4");
}
}This connection setup includes crucial elements:
- Proper error handling that throws exceptions rather than echoing errors.
- UTF-8 MB4 character set support for full Unicode compatibility.
- Clean encapsulation of the connection object.
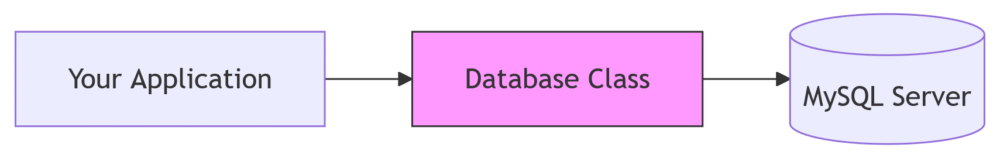
Connection flow helps understand what’s happening behind the scenes:
[Your Application] → [Database Class] → [MySQLi Connection] → [MySQL Server]
This link is private to the class, conforming with the principle of encapsulation. This way, outside code cannot mess with our database link and all queries pass through our controlled methods.
The Query Execution Engine: Power and Safety Combined
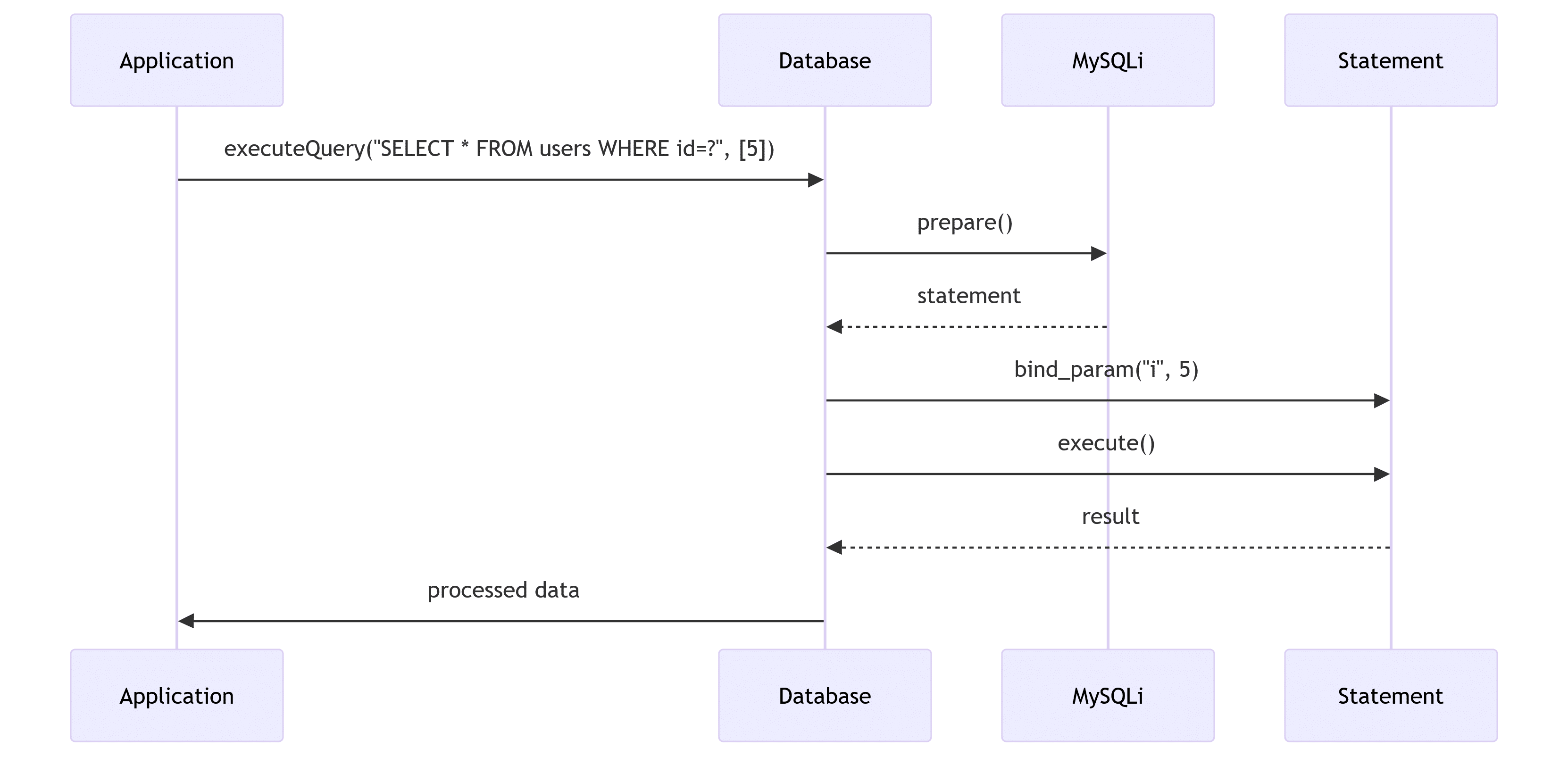
And now its time to do a deeper dive into the meat and drinking of our database class: the query execution. This is where magic happens – we transform ordinary database operations to something much cooler. The secret to running a modern database is a mix of prepared statements and configurable parameter binding.
- Simple queries without parameters
- Parameterized queries for security
- Different types of return values
Here’s how we implement this powerhouse feature:
public function executeQuery($sql, $params = []) {
$stmt = $this->connection->prepare($sql);
if (!$stmt) {
throw new RuntimeException(
"Query preparation failed: " . $this->connection->error
);
}
if (!empty($params)) {
$types = '';
foreach ($params as $param) {
if (is_int($param)) $types .= 'i';
elseif (is_double($param)) $types .= 'd';
else $types .= 's';
}
$stmt->bind_param($types, ...$params);
}
if (!$stmt->execute()) {
throw new RuntimeException(
"Query execution failed: " . $stmt->error
);
}
return $stmt;
}This method gives us:
- Automatic type detection for parameters
- Full prepared statement security
- Clean error handling
- Flexibility for any query type
The security benefits alone make this worth implementing. So try this comparison:
Unsafe Approach: SELECT * FROM users WHERE email = '$email' Our Secure Approach: SELECT * FROM users WHERE email = ?
Prepared statement effectively mitigates SQL Injection attacks which are one of the most prevalent and dangerous risk in web application vulnerabilities. It’s sort of like a bulletproof vest for your database operations.
Advanced Features for Elite Class
With everything in place, let’s enhance our database class with some functionality that real‐world applications expect:

Transaction Management
public function beginTransaction() {
$this->connection->begin_transaction();
}
public function commit() {
$this->connection->commit();
}
public function rollback() {
$this->connection->rollback();
}Helper Methods for Common Operations
public function fetchAll($sql, $params = []) {
$stmt = $this->executeQuery($sql, $params);
$result = $stmt->get_result();
return $result->fetch_all(MYSQLI_ASSOC);
}
public function fetchOne($sql, $params = []) {
$stmt = $this->executeQuery($sql, $params);
$result = $stmt->get_result();
return $result->fetch_assoc();
}These additions change our class from primary to professional grade. The marketing or transaction methods provide us with atomic operation ability, while the helper methods stop redundant result-fetching code.
Putting It All Together: A Real-World Example

Let’s see our database class in action with a complete user management example:
$db = new Database('localhost', 'app_user', 'secure_password', 'user_db');
try {
$db->beginTransaction();
// Create new user
$db->executeQuery(
"INSERT INTO users (email, password_hash) VALUES (?, ?)",
[$email, password_hash($password, PASSWORD_DEFAULT)]
);
// Get the new user's ID
$userId = $db->connection->insert_id;
// Create user profile
$db->executeQuery(
"INSERT INTO profiles (user_id, full_name) VALUES (?, ?)",
[$userId, $fullName]
);
$db->commit();
// Fetch the complete user data
$user = $db->fetchOne(
"SELECT u.*, p.full_name FROM users u
JOIN profiles p ON u.id = p.user_id
WHERE u.id = ?",
[$userId]
);
return $user;
} catch (Exception $e) {
$db->rollback();
error_log("User creation failed: " . $e->getMessage());
return false;
}This example shows:
- Transaction safety
- Secure parameter binding
- Convenient data retrieval
- Comprehensive error handling
The database class that we wrote today is a giant step in the way you manage databases. It’s not just about writing less code, but doing so in a higher quality, safer, and maintainable manner. This implementation gives you:
- Enterprise-grade security through prepared statements
- Professional error handling with proper exceptions
- Developer-friendly interfaces that simplify common tasks
- Transaction support for complex operations
- Performance optimizations baked right in
Conclusion
But the real magic happens when you apply this across many different projects. With a wave of the hand, suddenly all your applications enjoy this best practice. Bugs associated with the database go down, security improves and you can go faster in development.
In the competitive digital world of 2025, there’s no way that tools like this won’t be essential, rather than just a convenience. Take why we’re here and build on it. Customize for your use cases Add the functionality you need to enhance it for your use cases Watch how it changes the way you develop PHP apps.