Taking care of your iPhone in situations that can cause issues, like iPhone screen lock, is necessary. However, we can’t avoid every situation. We introduced you to some solutions for iPhone is disabled connect to iTunes.
We know that every new iOS model and version will bring some unique functionalities and new features to attract customers. It is the same for iOS 15, and iPhone 13 that comes up with unique functionalities, including how to unlock the iPhone is disabled connect to iTunes.
The new iPhone 13 model differs from the previous models in every aspect, whether its size, camera upgrade, design, display, small notch, etc. At the same time, the iOS 15 version comes up with many updated or new features that make this new version wonderful.
Steps to Resolve to Unlock Disabled iPhones
Part 1: How to Use iCloud To Unlock Your Disabled iPhone?
iCloud is a cloud computing service that allows users to store data, including music, photos, and documents, on remote servers to manage or share data with others. While using this method, you may need the iOS device of your friend, or you may face loss of data because you did not back up your data before your iPhone disabled.
A few steps can help you use iCloud if you do not unlock a disabled iPhone without iTunes. These few steps are mentioned below:
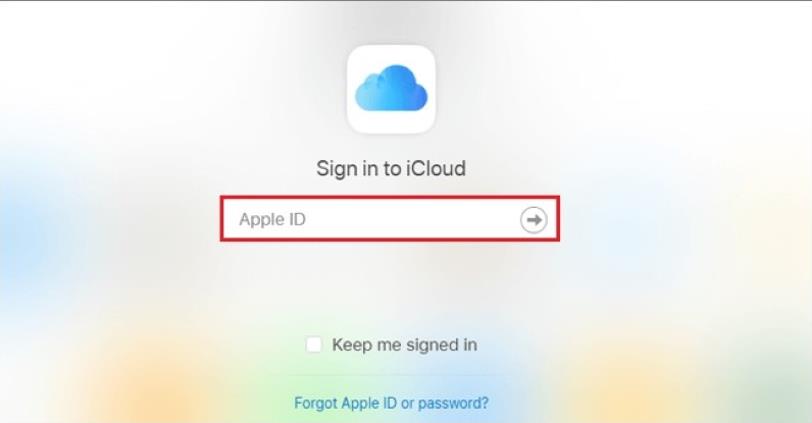
Step 1: Use your Apple ID and successfully log in to your iCloud account. After that, you will see the main menu having various applications, tap on “Find iPhone.”
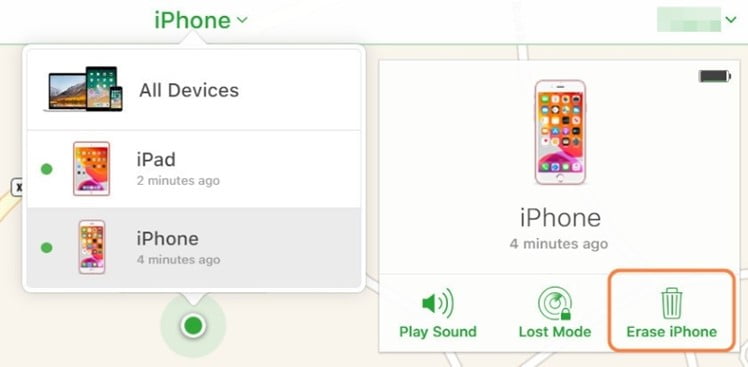
Step 2: You will view a map with all your devices mentioned, go to the top of the screen, choose “All Devices,” and select your iPhone among these devices.
Step 3: Now, choose “Erase iPhone” from the options available in the pop-up menu and confirm your actions. It will immediately reset your iPhone until it is turned on and has a good internet connection.
Part 2: Make Use of iTunes for Unlock Disabled iPhone
iTunes is a media library, client application, media player, internet radio broadcaster available for iTunes Store. You can use iTunes to download, purchase, organize, and play digital multimedia. You can also face issues using iTunes for iPhone disabled procedures, but it won’t work for new iOS users. It will also erase the real data from the iPhone once resetting is done.
The steps that you need to unlock disabled iPhone (iPhone screen lock) using iTunes are given below:
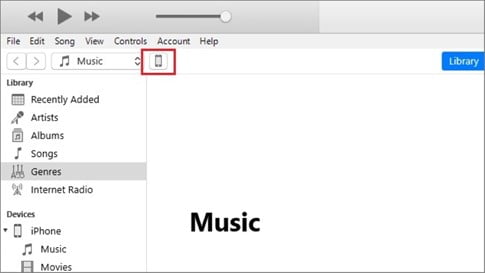
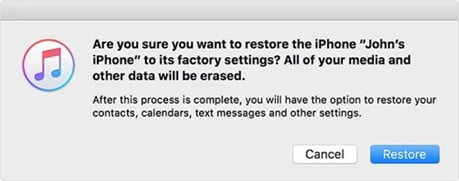
Step 1: Connect your iOS device with the computer you used to sync your iOS device previously. Now open iTunes and simply choose your device icon.
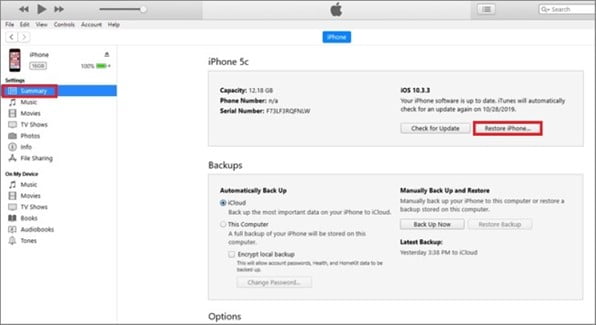
Step 2: Now, under the “Settings” section, click on the button “Restore iPhone.”
Step 3: iTunes will now contact the iPhone software update server and ask for user confirmation to restore. To go ahead, click on the button “Restore.” Now, wait until the whole process completes.
Part 3: Step-By-Step Guide for Beginners To Unlock Disabled iPhone Efficiently – Dr.Fone
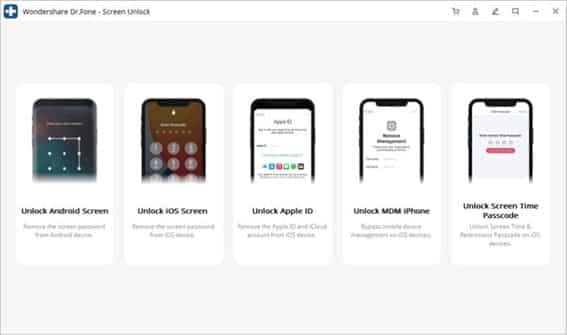
The most popular, efficient, and well-known software responsible for providing a complete mobile solution to its users is, Wondershare Dr.Fone. The best screen unlock software offers you a smooth screen unlock by following the basic steps. It can remove all kinds of passcodes, including 4- and 6-digit passcodes, Touch and Face ID, screen time, etc.
Wondershare Dr. Fone offers several other features that you should know to use this software for iPhone disabled how to unlock your iPhone. These features are:
- It can bypass the Apple ID and iCloud activation.
- Users with basic knowledge can use Dr.Fone easily to remove screen locks.
- It is fully compatible with all available models of iPhone and even with all updated iOS versions.
- It protects users’ data while removing their iPhone screen lock.
How to fix disabled iPhone using Wondershare Dr.Fone
Step 1: Launch the Software and Connect Device
First, launch the software Dr.Fone and choose the “Screen Unlock” tool among other available tools. Use a cable to connect both iPhone and PC, and select the program “Unlock iOS Screen.”
Step 2: Enable DFU Mode
Follow the given instructions on the software interface to successfully activate the DFU mode. If you could not activate the DFU or recovery mode, open the link at the bottom of the screen to activate the DFU mode.
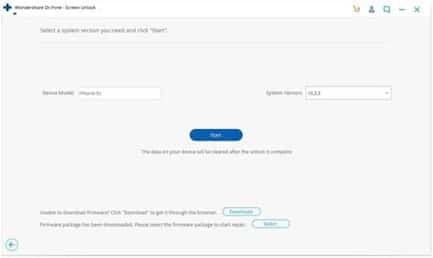
Step 3: Verify Device Information
In this step, the device information, including the system version and device model, will be displayed by Dr.Fone. Now tap on “Start” to initiate the firmware download for your device.
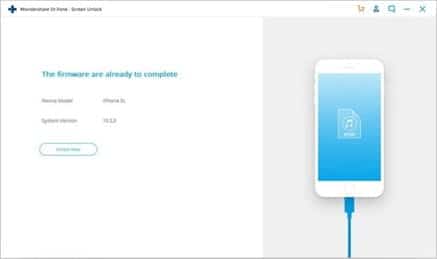
Step 4: Finish with iPhone Screen Unlock
If the firmware is downloaded, you can click “Unlock Now” to unlock the iPhone device and then finish the procedure.
Wrapping Up
The above discussion concludes the ways and methods that can be used as a solution for how to unlock disabled iPhones. These techniques include using iCloud and iTunes that provides an easy way for the iPhone to be disabled connect to iTunes. We have also discussed an efficient Wondershare Dr.Fone software to make a trouble-free iPhone screen unlock.
Check out: How To Fix the “iPhone is Disabled” Problem?