The landscape of software supply chain security has evolved significantly in recent years, with a critical emphasis on transparency and accountability. As part of this movement, the Cybersecurity and Infrastructure Security Agency (CISA) has introduced the Software Bill of Materials (SBOM) to enhance the understanding and management of software components. Within the CISA’s guidelines, there are six distinct SBOM types: Design, Source, Build, Analyzed, Deployed, and Runtime. Understanding the nuances of each type is crucial for a comprehensive approach to software security.
What is an SBOM?
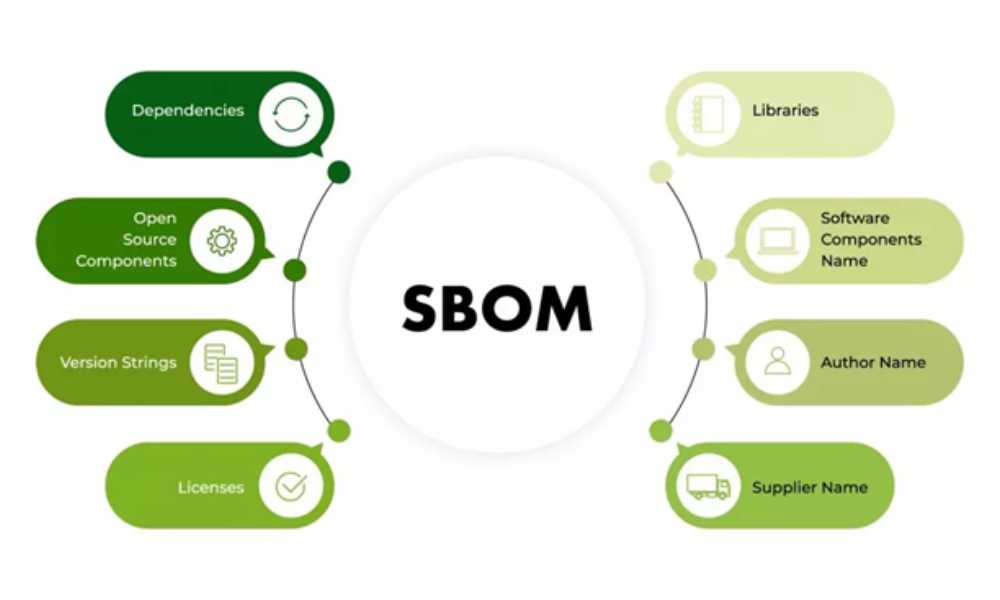
At its core, a Software Bill of Materials is a detailed inventory of the components that constitute a software product. It provides crucial insights into the various elements present within the software, including third-party libraries, open-source components, dependencies, and SBOM formats. This transparency aids in risk assessment, vulnerability management, and ensuring software supply chain security.
The 6 CISA SBOM Types
Software Bill of Materials (SBOM) has emerged as a critical instrument in understanding the complex composition of software products. The Cybersecurity and Infrastructure Security Agency (CISA) has delineated a comprehensive framework, categorizing SBOM into six distinct types. Each type unravels a unique aspect of a software product’s journey, shedding light on its components, dependencies, and vulnerabilities. Understanding these classifications is pivotal for organizations and individuals striving to fortify their cybersecurity measures. Let’s delve into each type and understand its significance in the software ecosystem:
Design SBOM
The Design SBOM captures the components planned for inclusion in a software product, offering insights before any code is written. Typically derived from design specifications, RFPs, or initial concepts, this SBOM serves as a foundational document shaping the early stages of software development. Understanding the intended composition at this stage aids in aligning the development process with the initial vision.
Check out: Is Generative AI Soon to Become a DevOps Cybersecurity Threat?
Source SBOM
Documenting the actual components used in building a software product, the Source SBOM encompasses source code, libraries, and frameworks. Created directly from the development environment and source files, it provides a comprehensive understanding of the software’s building blocks. This type offers insights into the actual materials employed in the developmental phase.
Build SBOM
Generated during the build process, the Build SBOM documents the components included in a released software artifact, such as an executable, package, or container image. Often derived from integrated intermediate Build and Source SBOMs, it presents a snapshot of the compiled product, which is crucial for validation and compliance.
Analyzed SBOM
The Analyzed SBOM emerges after a software artifact has been built. It involves analyzing the artifact to identify components, even those not explicitly declared in the build process. This type relies on heuristics to uncover implicit elements, providing insights into potential vulnerabilities that might have slipped through the development process.
Deployed SBOM
Focusing on components actually deployed in a production environment, the Deployed SBOM may be generated by scanning deployed systems or collecting SBOMs from various sources like build or CI/CD pipelines. This type offers a crucial understanding of the software’s real-world implementation, which is essential for risk assessment and ensuring compliance in live environments.
Runtime SBOM
The Runtime SBOM documents components that are actively running on a system at any given time. Generated through system process and memory usage monitoring, it provides real-time visibility into the software’s live state, aiding in identifying potential security vulnerabilities and ensuring system integrity.
Understanding and utilizing these six SBOM types are crucial steps in fortifying cybersecurity measures and ensuring software integrity throughout its lifecycle. From the conceptualization phase to real-world deployment and live system monitoring, each type offers a unique perspective, collectively contributing to a more secure and robust software ecosystem.
Making Sense of the Diversity
Each SBOM type serves a distinct purpose in the software development and deployment cycle. Understanding and utilizing these diverse SBOM types effectively is essential for a comprehensive and robust software supply chain security strategy.
Importance of Diversity
The diversity in SBOM types caters to different stages of software development and usage. From the conceptual phase with the Design SBOM to the operational phase with the Runtime SBOM, each type offers a unique perspective, contributing to a holistic understanding of the software’s lifecycle.
Enhanced Security and Transparency
By leveraging these SBOM types, organizations can bolster their security measures and enhance transparency within their software supply chain. Identifying vulnerabilities, monitoring changes, and understanding the software composition at various stages empower stakeholders to make informed decisions and take proactive security measures.
Risk Mitigation and Rapid Response
Understanding the diverse SBOM types enables better risk mitigation. With a detailed understanding of the software components, vulnerabilities, and their potential impact, organizations can swiftly respond to security threats and vulnerabilities, minimizing the potential damage.
Implementation and Best Practices
Efficient deployment of automated tools and standardized formats forms the cornerstone of SBOM integration, ensuring seamless generation and distribution of comprehensive software inventories. Collaborative efforts across the software supply chain amplify the efficacy of SBOMs, fostering a culture of transparency and shared responsibility, essential in fortifying cybersecurity measures and navigating vulnerability landscapes effectively.
Automated Tools and Standardized Formats
Employing specialized tools and adopting industry-standard formats, such as SPDX, streamlines the generation and sharing of SBOMs. This step is fundamental for ensuring consistency and compatibility across the software supply chain.
Collaboration Across the Supply Chain
Effective SBOM implementation relies on collaboration among stakeholders within the software supply chain. Encouraging transparency and sharing SBOMs can fortify cybersecurity measures and streamline vulnerability management.
Conclusion
The CISA’s six different SBOM types serve as a comprehensive framework for understanding software composition, vulnerabilities, and overall security posture. Embracing these types empowers organizations to navigate the complex software supply chain, mitigate risks, and fortify their security measures at every stage of the software lifecycle. By integrating these SBOM types into their practices, companies can ensure a more secure and transparent software ecosystem, ultimately benefiting both their operations and the end users. Understanding the nuances and leveraging the capabilities of each SBOM type will pave the way for a more resilient and secure software landscape.
Check out: The Importance Of Cybersecurity In The Nonprofit Sectors