Shared and Dedicated Internet: Choosing the right internet connection is crucial for both individuals and businesses, as it directly impacts productivity, reliability, and overall user experience. The two primary types of internet access—Shared vs Dedicated Internet Internet Access—offer distinct benefits depending on the user’s requirements. Shared Internet Access is typically more affordable and is suitable for light usage, such as browsing or casual streaming, where high-speed consistency is less critical.
When comparing Shared vs Dedicated Internet, the latter is designed for users who need guaranteed, high-performance connections—ideal for businesses relying on constant, uninterrupted access for video conferencing, cloud computing, or large data transfers. Understanding the key differences between Shared vs Dedicated Internet helps you assess needs accurately, ensuring you select the right connection type for your usage patterns, budget, and performance requirements. This article explores these critical distinctions in depth, providing actionable insights to inform your decision.
1. What is Shared Internet Access?
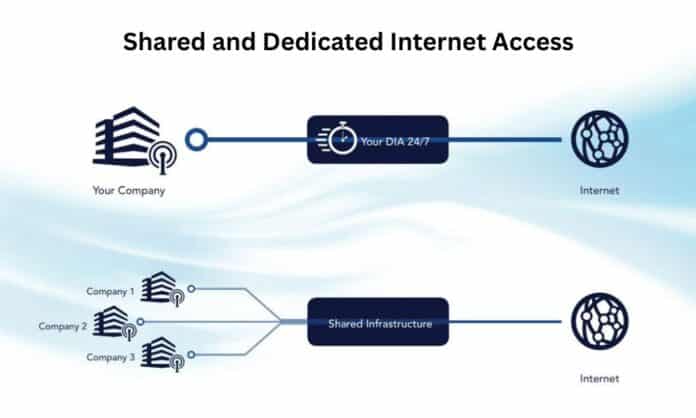
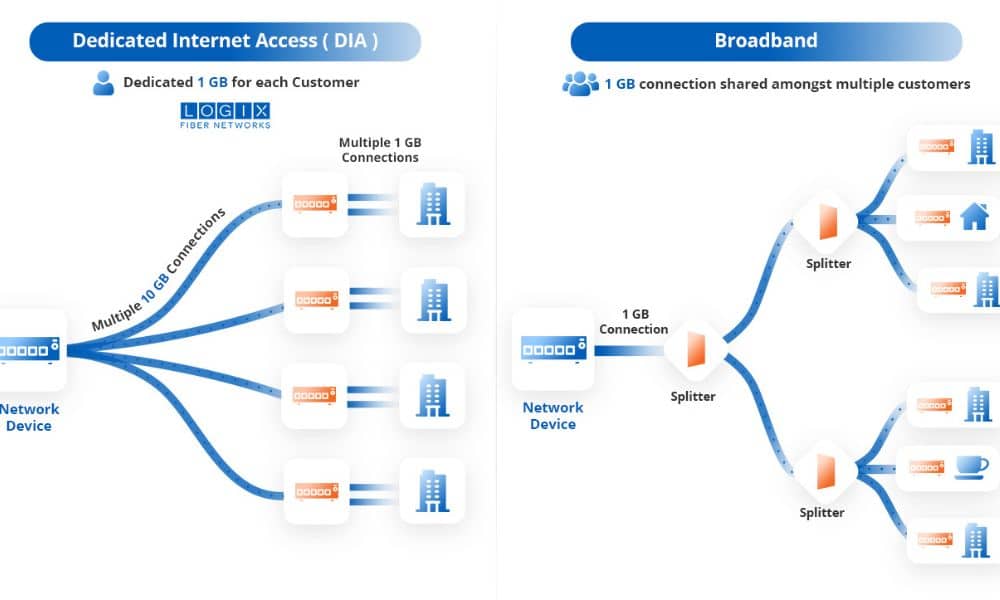
Shared Internet Access refers to a connection where multiple users share the same bandwidth. This is commonly seen in residential settings or small businesses where high-speed internet is not a critical requirement.
Shared connections are cost-effective and easy to set up, making them appealing for users with basic internet needs. However, the shared nature means that during peak usage times, the internet speed can fluctuate, leading to potential slowdowns.
Key Characteristics of Shared Internet Access:
- Cost-Effective: Generally more affordable due to shared resources.
- Variable Speeds: Performance can degrade during peak usage times.
- Suitable for Basic Use: Ideal for browsing, streaming, and light work tasks.
- Limited Control: Less flexibility in managing bandwidth and performance.
2. What is Dedicated Internet Access?
Dedicated Internet Access (DIA) provides a private connection where the bandwidth is exclusively allocated to a single user or organization. This setup ensures consistent and high-speed internet performance, regardless of external traffic.
DIA is particularly beneficial for businesses that rely on uninterrupted internet access for operations such as cloud computing, video conferencing, and large data transfers.
Key Characteristics of Dedicated Internet Access:
Dedicated Internet Access (DIA) provides exclusive bandwidth, ensuring reliable, consistent speeds without slowdowns. It’s ideal for businesses requiring uninterrupted service, enhanced security, and scalable performance for critical operations.
- Consistent Speeds: Guaranteed bandwidth ensures stable performance.
- Enhanced Security: Dedicated lines reduce exposure to external threats.
- Scalability: Easier to upgrade as business needs grow.
- Service Level Agreements (SLAs): Providers often offer SLAs guaranteeing uptime and support.
3. Comparing Shared and Dedicated Internet Access
| Feature | Shared Internet Access | Dedicated Internet Access |
|---|---|---|
| Bandwidth | Shared among multiple users | Exclusively allocated |
| Speed Consistency | Variable, especially during peak times | Consistent and reliable |
| Security | Lower, due to shared resources | Higher, with private connections |
| Cost | More affordable | Higher, due to dedicated resources |
| Ideal For | Casual browsing and light usage | Business operations and heavy usage |
4. When to Choose Shared Internet Access
Shared Internet Access is ideal for individuals or small businesses with basic internet needs, such as browsing, streaming, and light work. It’s cost-effective and works well when high-speed consistency isn’t critical.
Shared Internet Access is suitable for:
- Individuals or Small Households: Where internet usage is minimal and cost is a significant factor.
- Non-Critical Applications: For activities like browsing, streaming, and social media.
- Temporary Setups: Such as events or short-term projects where high-speed internet is not essential.
5. When to Choose Dedicated Internet Access
- Business Operations Depend on Internet: For tasks like cloud services, VoIP, and video conferencing.
- High-Speed and Reliability are Crucial: Ensuring consistent performance for critical applications.
- Security is a Priority: Protecting sensitive data and maintaining privacy.
- Scalability is Needed: Ability to upgrade bandwidth as business grows
Conclusion: Shared vs Dedicated Internet
Choosing between Shared and Dedicated Internet Access largely depends on your specific needs and budget. Shared connections are an affordable option suitable for individuals or small businesses that use the internet for basic tasks like browsing, streaming, and social media Performance can fluctuate, especially during peak hours when other users share the bandwidth, leading to slower speeds.
In contrast of Shared vs Dedicated Internet access, Dedicated Internet Access is ideal for businesses or users who rely on consistent, high-speed internet for mission-critical operations such as cloud computing, VoIP, or video conferencing. While more expensive, DIA offers guaranteed speeds and greater reliability, ensuring that your internet connection remains uninterrupted, even during times of high demand. The choice ultimately depends on whether you prioritize affordability or the need for a stable, high-performance connection.
Check out: Choose the Secured Dedicated Server in UAE from Serverwala